Why 7 if we can do it with 3 Least privileged access is to have nothing more than the permissions you need to complete your task. Every time I get to a new customer, and I need administrative access to […]
Over a decade of expertise in Active Directory, infrastructure, and security. Deep dive into AD Tier Model, RBAC and PowerShell automation
Least privileged access is to have nothing more than the permissions you need in order to complete your task.
Restricting access rights for users, accounts, and computing processes to only those resources absolutely required to perform routine, legitimate activities.
Just giving a user account or process only those privileges which are essential to perform its intended function.
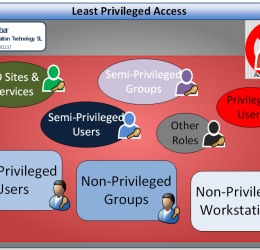
Why 7 if we can do it with 3 Least privileged access is to have nothing more than the permissions you need to complete your task. Every time I get to a new customer, and I need administrative access to […]