In the Building Admin Area (Tier0) we created most of the objects required on our Admin Area (Tier0). Now we need delegate Admin Area (Tier0) by configuring all required permissions and rights based on the roles defined in our Delegation Mode.
- Semi-Privileged User Management (UM)
- Semi-Privileged Group Management (GM)
- Privileged User Management (PUM)
- Privileged Group Management (PGM)
- Privileged Infrastructure Services Management (PSIM)
- Privileged Access Workstation Management (PAWM)
- Privileged Service Account Management (PSAM)
- Group Policy Management
- Directory Replication
- Infrastructure Administration
- AD Administration
Semi-Privileged User Management (UM)
UM group (User Management) will be able to create and modify Semi-Privileged user objects within this container, but will not have rights over any Privileged user.
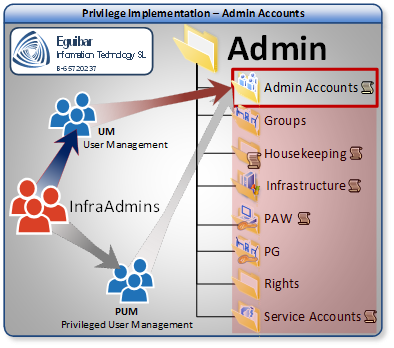
Once more a wrapper function is needed. EguibarIT.Delegation PowerShell Module provides CMDlets to delegate User creation(Set-AdAclCreateDeleteUser), Reset user password (Set-AdAclResetUserPassword), Change User Password (Set-AdAclChangeUserPassword), Enable, Disable User (Set-AdAclEnableDisableUser), Unlock User (Set-AdAclUnlockUser), manage Account Restrictions (Set-AdAclUserAccountRestriction) & UserLogonInfo ( Set-AdAclUserLogonInfo). All these CMDlets are wrapped into a single CMDlet called Set-AdAclDelegateUserAdmin. A similar wrapper and supporting functions exist for GAL.
[pastacode manual=”%3Ccode%3E%23%20Delegation%20to%20ADMIN%20area%20(Tier%200)%0A%0A%20%20%20%20%20%20%20%20Write-Verbose%20-Message%20’Delegate%20Admin%20Area…’%0A%0A%20%20%20%20%20%20%20%20%23%20Computer%20objects%20within%20this%20ares%20MUST%20have%20read%20access%2C%20otherwise%20GPO%20will%20not%20apply%0A%0A%20%20%20%20%20%20%20%20%23%20UM%20-%20Semi-Privileged%20User%20Management%0A%20%20%20%20%20%20%20%20Set-AdAclDelegateUserAdmin%20-Group%20%24SL_UM.SamAccountName%20-LDAPpath%20%24ItAdminAccountsOuDn%0A%20%20%20%20%20%20%20%20Set-AdAclDelegateGalAdmin%20%20-Group%20%24SL_UM.SamAccountName%20-LDAPpath%20%24ItAdminAccountsOuDn%3C%2Fcode%3E” provider=”manual” lang=”php”/]Semi-Privileged Group Management (GM)
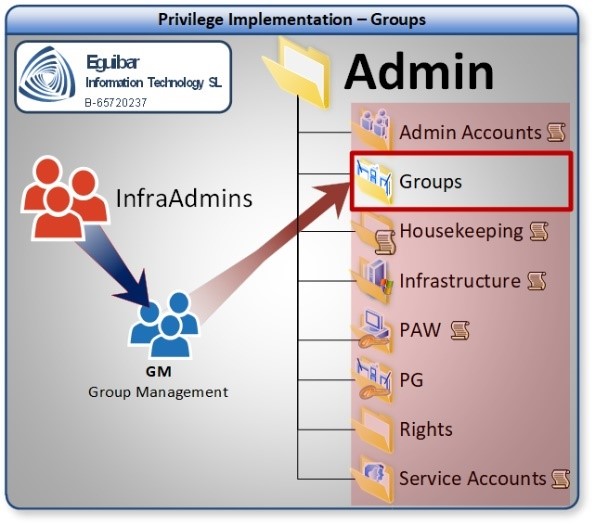
“PGM (Privileged Group Management)” group will be able to create and modify group objects within the groups container.
Privileged User Management (PUM)
Only “PUM (Privileged User Management)” group will be able to modify Privileged user objects within this container.
[pastacode manual=”%3Ccode%3E%23%20Delegation%20to%20ADMIN%20area%20(Tier%200)%0A%0A%20%20%20%20%20%20%20%20Write-Verbose%20-Message%20’Delegate%20Admin%20Area…’%0A%0A%20%20%20%20%20%20%20%20%23%20Computer%20objects%20within%20this%20ares%20MUST%20have%20read%20access%2C%20otherwise%20GPO%20will%20not%20apply%0A%0A%20%20%20%20%20%20%20%20%23%20PUM%20-%20Privileged%20User%20Management%0A%20%20%20%20%20%20%20%20Set-AdAclDelegateUserAdmin%20-Group%20%24SL_PUM.SamAccountName%20-LDAPpath%20%24ItAdminAccountsOuDn%0A%20%20%20%20%20%20%20%20Set-AdAclDelegateGalAdmin%20%20-Group%20%24SL_PUM.SamAccountName%20-LDAPpath%20%24ItAdminAccountsOuDn%3C%2Fcode%3E” provider=”manual” lang=”php”/]Privileged Group Management (PGM)
[pastacode manual=”%3Ccode%3E%23%20Delegation%20to%20ADMIN%20area%20(Tier%200)%0A%0A%20%20%20%20%20%20%20%20Write-Verbose%20-Message%20’Delegate%20Admin%20Area…’%0A%0A%20%20%20%20%20%20%20%20%23%20PGM%20-%20Privileged%20Group%20Management%0A%20%20%20%20%20%20%20%20%23%20Create%2FDelete%20Groups%0A%20%20%20%20%20%20%20%20Set-AdAclCreateDeleteGroup%20-Group%20%24SL_PGM.SamAccountName%20-LDAPPath%20%24ItPrivGroupsOUDn%0A%20%20%20%20%20%20%20%20Set-AdAclCreateDeleteGroup%20-Group%20%24SL_PGM.SamAccountName%20-LDAPPath%20%24ItRightsOuDn%0A%20%20%20%20%20%20%20%20%23%20Change%20Group%20Properties%0A%20%20%20%20%20%20%20%20Set-AdAclChangeGroup%20-Group%20%24SL_PGM.SamAccountName%20-LDAPPath%20%24ItPrivGroupsOUDn%0A%20%20%20%20%20%20%20%20Set-AdAclChangeGroup%20-Group%20%24SL_PGM.SamAccountName%20-LDAPPath%20%24ItRightsOuDn%3C%2Fcode%3E” provider=”manual” lang=”php”/]Privileged Infrastructure Services Management (PSIM)
Take patch management as an example. All servers and computers within “Admin Area”/Tier0 must be regularly patched, but those cannot share the same patching solution as for regular PCs or servers. The patching service must be configured exclusively for this Area/Tier, so all AD objects required for this purpose should be within Admin Area, having the infrastructure part (as it can be the computer object for the patching server) hosted here.
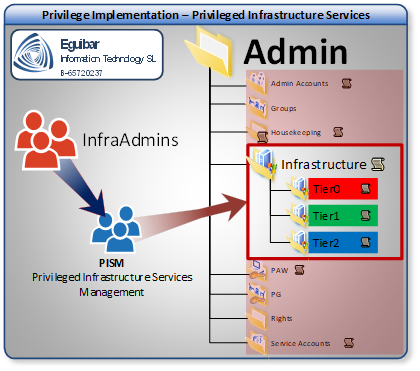
Only “Privileged Infrastructure Services Management” group can create and delete computer objects within this container. Here, once more, got the requirement of a wrapper function. In order to delegate management of a computer, we need to Create/Delete Computers (Set-AdAclCreateDeleteComputer), Reset Computer Password (Set-AdAclResetComputerPassword), Change Computer Password (Set-AdAclChangeComputerPassword), Validated write to DNS host name (Set-AdAclValidateWriteDnsHostName), Validated write to SPN (Set-AdAclValidateWriteSPN), Change Computer Account Restriction (Set-AdAclComputerAccountRestriction), Change DNS Hostname Info (Set-AdAclDnsInfo), Change MS TerminalServices info (Set-AdAclMsTsGatewayInfo), Access to BitLocker & TMP info (Set-AdAclBitLockerTPM), Grant the right to delete computers from default container. Move Computers (Set-DeleteOnlyComputer) and Set LAPS (Set-AdAclLaps). This function is ideal for any container which deals with Computer objects.
[pastacode manual=”%3Ccode%3E%20%23%20PISM%20-%20Privileged%20Infrastructure%20Services%20Management%0A%20%20%20%20%20%20%20%20%23%20Create%2FDelete%20Computers%0A%20%20%20%20%20%20%20%20Set-AdAclDelegateComputerAdmin%20-Group%20%24SL_PISM.SamAccountName%20-LDAPPath%20%24ItInfraT0OuDn%20%20%20%20%20%20-QuarantineDN%20%24ItQuarantineOuDn%0A%20%20%20%20%20%20%20%20Set-AdAclDelegateComputerAdmin%20-Group%20%24SL_PISM.SamAccountName%20-LDAPPath%20%24ItInfraT1OuDn%20%20%20%20%20%20-QuarantineDN%20%24ItQuarantineOuDn%0A%20%20%20%20%20%20%20%20Set-AdAclDelegateComputerAdmin%20-Group%20%24SL_PISM.SamAccountName%20-LDAPPath%20%24ItInfraT2OuDn%20%20%20%20%20%20-QuarantineDN%20%24ItQuarantineOuDn%0A%20%20%20%20%20%20%20%20Set-AdAclDelegateComputerAdmin%20-Group%20%24SL_PISM.SamAccountName%20-LDAPPath%20%24ItInfraStagingOuDn%20-QuarantineDN%20%24ItQuarantineOuDn%0A%3C%2Fcode%3E” provider=”manual” lang=”php”/]Privileged Access Workstation Management (PAWM)
As part of the administration separation between normal users and admin users, a secure host, or “Privileged Access Workstation”, must exist in order to fully separate a standard computer from the specific privileged machine used for domain privileged maintenance. Each of the defined tiers within this model (Admin/Tier0, Servers/Tier1 & Sites/Tier2) will have its own set of PAWs for administration; is not permitted to share PAWs between Areas/Tiers.
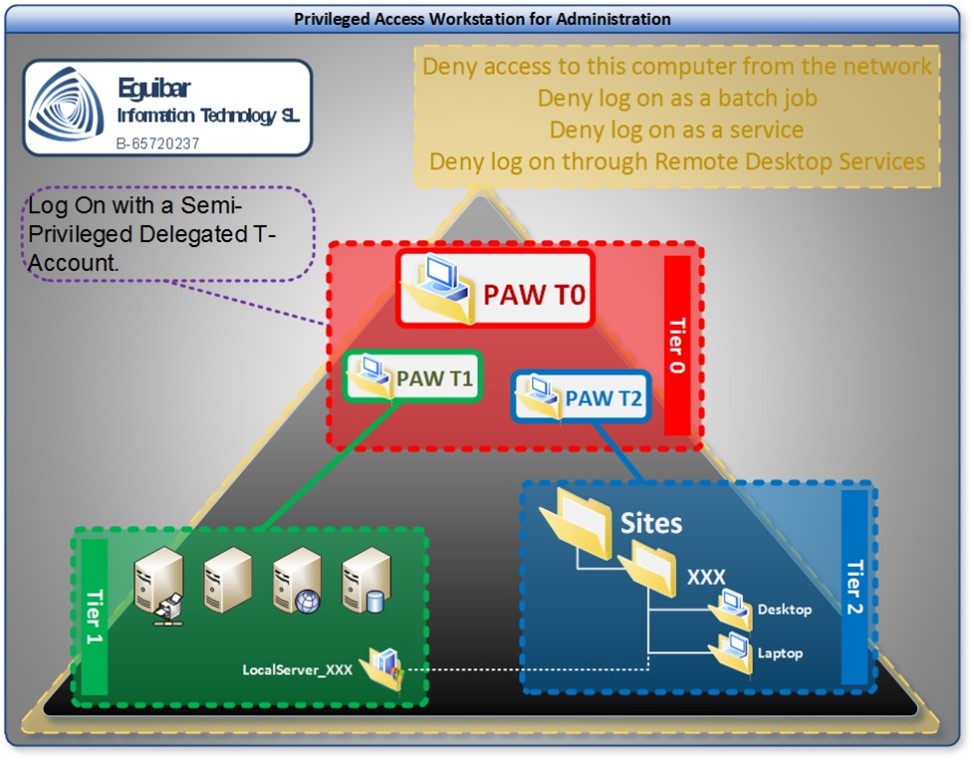
Only “PAW Management” group will be able to create and modify computer objects within this container, and this team is responsible for the maintenance of the mentioned assets. Those assets will be organized on their own sub-ou depending on which tier are assigned to.
As we are speaking of a “Computer” container, the Set-AdAclDelegateComputerAdmin wrapper function can be used.
[pastacode manual=”%3Ccode%3E%23%20PAWM%20-%20Privileged%20Access%20Workstation%20Management%0A%20%20%20%20%20%20%20%20Set-AdAclDelegateComputerAdmin%20-Group%20%24SL_PAWM.SamAccountName%20-LDAPPath%20%24ItPawT0OuDn%20-QuarantineDN%20%24ItQuarantineOuDn%0A%20%20%20%20%20%20%20%20Set-AdAclDelegateComputerAdmin%20-Group%20%24SL_PAWM.SamAccountName%20-LDAPPath%20%24ItPawT1OuDn%20-QuarantineDN%20%24ItQuarantineOuDn%0A%20%20%20%20%20%20%20%20Set-AdAclDelegateComputerAdmin%20-Group%20%24SL_PAWM.SamAccountName%20-LDAPPath%20%24ItPawT2OuDn%20-QuarantineDN%20%24ItQuarantineOuDn%0A%20%20%20%20%20%20%20%20Set-AdAclDelegateComputerAdmin%20-Group%20%24SL_PAWM.SamAccountName%20-LDAPPath%20%24ItPawStagingOuDn%20-QuarantineDN%20%24ItQuarantineOuDn%0A%3C%2Fcode%3E” provider=”manual” lang=”php”/]Privileged Service Account Management (PSAM)
Service account is a security principal with privileges above normal and special granted rights, as it may be the “Logon as a Batch Process” or “Logon as a Service” or “Interact as Part of the OS” but not exclusively; these rights are quite common for Service Accounts, and is used by applications to run properly and execute privileged routines or windows services without user intervention.
Service Accounts are un-personal, so nobody is supposed to choose a password to be used, except for the person who created the Service Account; this is the reason to use a strong convention for passwords of Service Accounts.
A Service Account must:
- Follow the corporate naming conventions
- Have all (within possible) attributes completed (First Name, Last Name, Address, etc.)
- Reside within the corresponding AD container (Service Accounts OU)
- Set the “employeeType” attribute to ServiceAccount
- Use the less privileges as possible
- Be jealously keep
- Use a Very Strong Password
- Not contain name, last name, userID or any other attribute (full or partial) within the password
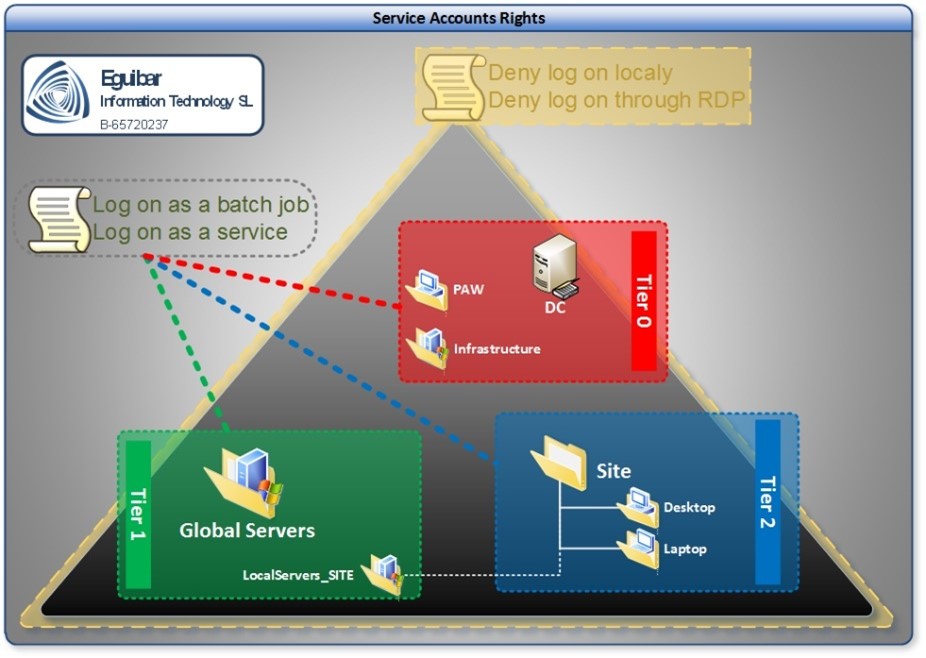
Following the delegation model, a Security Global Group must be created for each of the tiers, following current naming conventions, in the corresponding container (within the administrative OU tree, on the group container OU) and all service accounts must be part of their corresponding group. If a service account is not member of any of these groups, the required service extended rights (Logon as a Service & Logon as a Batch Job) will not be granted. On the other hand, any user object placed inside of any of these containers will become a Service Account. Only “Privileged ServiceAccount Management” group will be able to create and modify user objects, GroupManagedServiceAccounts and ManagedServiceAccounts.
[pastacode manual=”%3Ccode%3E%23%20PSAM%20-%20Privileged%20Service%20Account%20Management%20-%20Create%2FDelete%20Managed%20Service%20Accounts%20%26%20Standard%20user%20service%20accounts%0A%20%20%20%20%20%20%20%20%23%20Managed%20Service%20Accounts%20%22Default%20Container%22%0A%20%20%20%20%20%20%20%20%24parameters%20%3D%20%40%7B%0A%20%20%20%20%20%20%20%20%20%20%20%20Group%20%20%20%20%3D%20%24SL_PSAM.SamAccountName%0A%20%20%20%20%20%20%20%20%20%20%20%20LDAPPath%20%3D%20(‘CN%3DManaged%20Service%20Accounts%2C%7B0%7D’%20-f%20%24AdDn)%0A%20%20%20%20%20%20%20%20%7D%0A%20%20%20%20%20%20%20%20Set-AdAclCreateDeleteGMSA%20%20%20%20%20%20%20%40parameters%0A%20%20%20%20%20%20%20%20Set-AdAclCreateDeleteMSA%20%20%20%20%20%20%20%20%40parameters%0A%0A%20%20%20%20%20%20%20%20%23%20TIER%200%0A%20%20%20%20%20%20%20%20%24parameters%20%3D%20%40%7B%0A%20%20%20%20%20%20%20%20%20%20%20%20Group%20%20%20%20%3D%20%24SL_PSAM.SamAccountName%0A%20%20%20%20%20%20%20%20%20%20%20%20LDAPPath%20%3D%20%24ItSAT0OuDn%0A%20%20%20%20%20%20%20%20%7D%0A%20%20%20%20%20%20%20%20Set-AdAclCreateDeleteGMSA%20%20%20%20%20%20%20%40parameters%0A%20%20%20%20%20%20%20%20Set-AdAclCreateDeleteMSA%20%20%20%20%20%20%20%20%40parameters%0A%20%20%20%20%20%20%20%20Set-AdAclCreateDeleteUser%20%20%20%20%20%20%20%40parameters%0A%20%20%20%20%20%20%20%20Set-AdAclResetUserPassword%20%20%20%20%20%20%40parameters%0A%20%20%20%20%20%20%20%20Set-AdAclChangeUserPassword%20%20%20%20%20%40parameters%0A%20%20%20%20%20%20%20%20Set-AdAclUserGroupMembership%20%20%20%20%40parameters%0A%20%20%20%20%20%20%20%20Set-AdAclUserAccountRestriction%20%40parameters%0A%20%20%20%20%20%20%20%20Set-AdAclUserLogonInfo%20%20%20%20%20%20%20%20%20%20%40parameters%0A%0A%20%20%20%20%20%20%20%20%23%20TIER%201%0A%20%20%20%20%20%20%20%20%24parameters%20%3D%20%40%7B%0A%20%20%20%20%20%20%20%20%20%20%20%20Group%20%20%20%20%3D%20%24SL_PSAM.SamAccountName%0A%20%20%20%20%20%20%20%20%20%20%20%20LDAPPath%20%3D%20%24ItSAT1OuDn%0A%20%20%20%20%20%20%20%20%7D%0A%20%20%20%20%20%20%20%20Set-AdAclCreateDeleteGMSA%20%20%20%20%20%20%20%40parameters%0A%20%20%20%20%20%20%20%20Set-AdAclCreateDeleteMSA%20%20%20%20%20%20%20%20%40parameters%0A%20%20%20%20%20%20%20%20Set-AdAclCreateDeleteUser%20%20%20%20%20%20%20%40parameters%0A%20%20%20%20%20%20%20%20Set-AdAclResetUserPassword%20%20%20%20%20%20%40parameters%0A%20%20%20%20%20%20%20%20Set-AdAclChangeUserPassword%20%20%20%20%20%40parameters%0A%20%20%20%20%20%20%20%20Set-AdAclUserGroupMembership%20%20%20%20%40parameters%0A%20%20%20%20%20%20%20%20Set-AdAclUserAccountRestriction%20%40parameters%0A%20%20%20%20%20%20%20%20Set-AdAclUserLogonInfo%20%20%20%20%20%20%20%20%20%20%40parameters%0A%0A%20%20%20%20%20%20%20%20%23%20TIER%202%0A%20%20%20%20%20%20%20%24parameters%20%3D%20%40%7B%0A%20%20%20%20%20%20%20%20%20%20%20%20Group%20%20%20%20%3D%20%24SL_PSAM.SamAccountName%0A%20%20%20%20%20%20%20%20%20%20%20%20LDAPPath%20%3D%20%24ItSAT2OuDn%0A%20%20%20%20%20%20%20%20%7D%0A%20%20%20%20%20%20%20%20Set-AdAclCreateDeleteGMSA%20%20%20%20%20%20%20%40parameters%0A%20%20%20%20%20%20%20%20Set-AdAclCreateDeleteMSA%20%20%20%20%20%20%20%20%40parameters%0A%20%20%20%20%20%20%20%20Set-AdAclCreateDeleteUser%20%20%20%20%20%20%20%40parameters%0A%20%20%20%20%20%20%20%20Set-AdAclResetUserPassword%20%20%20%20%20%20%40parameters%0A%20%20%20%20%20%20%20%20Set-AdAclChangeUserPassword%20%20%20%20%20%40parameters%0A%20%20%20%20%20%20%20%20Set-AdAclUserGroupMembership%20%20%20%20%40parameters%0A%20%20%20%20%20%20%20%20Set-AdAclUserAccountRestriction%20%40parameters%0A%20%20%20%20%20%20%20%20Set-AdAclUserLogonInfo%20%20%20%20%20%20%20%20%20%20%40parameters%3C%2Fcode%3E” provider=”manual” lang=”php”/]Group Policy Management
This container is where all the Group Policy Objects (GPO) reside, no matter to which Tier/Area these objects belong to. By default, the domain Administrator is the owner of these container, thus having full control over all contained objects.
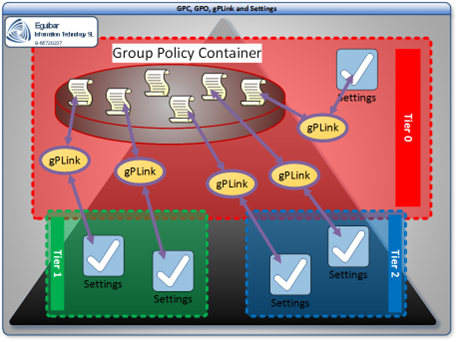
Because of the implied rights the Administration account has, having a solely delegated GPO rights to a group is a must. The GPO Admin group has these rights delegated, acting as a full administrator only within the GPC.
This role is the equivalent as the built-in Administrator but limited only to the mentioned container. This role is able to:
- Create/Delete GPO
- Create/Delete GPLinks
- Manage GPOptions (Inheritance)
Directory Replication
[pastacode manual=”%3Ccode%3E%20%23%20Delegate%20Directory%20Replication%20Rights%0A%20%20%20%20%20%20%20%20Set-AdDirectoryReplication%20-Group%20%24SL_DirReplRight.SamAccountName%3C%2Fcode%3E” provider=”manual” lang=”php”/]Infrastructure Administration
This group is getting additional permissions within AD. For example, this group is the ONLY group having permissions to Create/Delete Organizational Units, Sites, Subnets, SiteLinks or Transfer FSMO roles.
[pastacode manual=”%3Ccode%3E%20%23%20Infrastructure%20Admins%0A%20%20%20%20%20%20%20%20%23%20Organizational%20Units%20at%20domain%20level%0A%20%20%20%20%20%20%20%20Set-AdAclCreateDeleteOU%20%20%20%20%20%20-Group%20%24SL_InfraRight.SamAccountName%20-LDAPPath%20%24AdDn%0A%20%20%20%20%20%20%20%20%23%20Organizational%20Units%20at%20Admin%20area%0A%20%20%20%20%20%20%20%20Set-AdAclCreateDeleteOU%20%20%20%20%20%20-Group%20%24SL_InfraRight.SamAccountName%20-LDAPPath%20%24ItAdminOuDn%0A%20%20%20%20%20%20%20%20%23%20Subnet%20Configuration%20Container%0A%20%20%20%20%20%20%20%20%23%20Create%2FDelete%20Subnet%0A%20%20%20%20%20%20%20%20Set-AdAclCreateDeleteSubnet%20%20-Group%20%24SL_InfraRight.SamAccountName%0A%20%20%20%20%20%20%20%20%23%20Site%20Configuration%20Container%0A%20%20%20%20%20%20%20%20%23%20Create%2FDelete%20Sites%0A%20%20%20%20%20%20%20%20Set-AdAclCreateDeleteSite%20%20%20%20-Group%20%24SL_InfraRight.SamAccountName%0A%20%20%20%20%20%20%20%20%23%20Site-Link%20Configuration%20Container%0A%20%20%20%20%20%20%20%20%23%20Create%2FDelete%20Site-Link%0A%20%20%20%20%20%20%20%20Set-AdAclCreateDeleteSiteLink%20-Group%20%24SL_InfraRight.SamAccountName%0A%20%20%20%20%20%20%20%20%23%20Transfer%20FSMO%20roles%0A%20%20%20%20%20%20%20%20Set-AdAclFSMOtransfer%20-Group%20%24SL_TransferFSMOright.SamAccountName%20-FSMOroles%20’Schema’%2C%20’Infrastructure’%2C%20’DomainNaming’%2C%20’RID’%2C%20’PDC’%0A%3C%2Fcode%3E” provider=”manual” lang=”php”/]AD Administration
This group has the permissions to change many of the existing objects, but create/delete is reserved for infrastructure admins.
[pastacode manual=”%3Ccode%3E%23%20AD%20Admins%0A%20%20%20%20%20%20%20%20%23%20Domain%20Controllers%20management%0A%20%20%20%20%20%20%20%20Set-AdAclDelegateComputerAdmin%20-Group%20%24SL_AdRight.SamAccountName%20-LDAPPath%20%24DCsOuDn%20%20%20%20%20%20%20%20%20%20-QuarantineDN%20%24ItQuarantineOuDn%0A%20%20%20%20%20%20%20%20%23%20Delete%20computers%20from%20default%20container%0A%20%20%20%20%20%20%20%20Set-DeleteOnlyComputer%20%20%20%20%20%20%20%20%20-Group%20%24SL_AdRight.SamAccountName%20-LDAPPath%20%24ItQuarantineOuDn%0A%20%20%20%20%20%20%20%20%23%20Subnet%20Configuration%20Container%7C%0A%20%20%20%20%20%20%20%20%23%20Change%20Subnet%0A%20%20%20%20%20%20%20%20Set-AdAclChangeSubnet%20%20%20%20%20%20%20%20%20%20%20-Group%20%24SL_AdRight.SamAccountName%0A%20%20%20%20%20%20%20%20%23%20Site%20Configuration%20Container%0A%20%20%20%20%20%20%20%20%23%20Change%20Site%0A%20%20%20%20%20%20%20%20Set-AdAclChangeSite%20%20%20%20%20%20%20%20%20%20%20%20%20-Group%20%24SL_AdRight.SamAccountName%0A%20%20%20%20%20%20%20%20%23%20Site-Link%20Configuration%20Container%0A%20%20%20%20%20%20%20%20%23%20Change%20SiteLink%0A%20%20%20%20%20%20%20%20Set-AdAclChangeSiteLink%20%20%20%20%20%20%20%20%20-Group%20%24SL_AdRight.SamAccountName%3C%2Fcode%3E” provider=”manual” lang=”php”/]After completing the delegation, we can Configure Admin Area (Tier0).