Role Based Access Control model (RBAC)
The Role Based Access Control model, or RBAC, is the model which will grant or revoke permissions and rights to semi-privileged users. This is effectively another way to call the Delegation Model. Any “Access Control” model relies on a set of tasks. These tasks are group together. Then this group gets populated to provide controlled access to the resources.
An RBAC consist of several components, depending on the role itself:
- A resource (or several) to protect
- Access Control List associated to the resource
- A Group which is reference on the ACL
- A Group for the security principals which need access to the resource
- Security Principals (users)
The key factors when designing this model are Least Privileged Access and Segregation of Duties. This is why most of our resources do not provide enough security, or at least flexibility. Having a single role (like Administrator or root) will jeopardize the security. Yes, we have all that we need. Even worst, way more of what we need. Other point to consider; security principal directly defined into an ACL, no way. So we need extra groups and nesting strategy. But how many groups? Enough to abstract the resource/ACL from the security principal, but the least to maintain control and security. The use of RBAC to manage user privileges (computer permissions) within a single system or application is widely accepted as a best practice.
SQL database example
Lets imagine I need access to a SQL database. Of course the Administrator has “Full Control” over the db, but not limited to it. It also has the same control over the server hosting the DB. This example is the opposite of Least Privileged Access. In this example we can consider 6 roles, just as an example.
- Server Administrator. Full admin access to the server hosting SQL
- db_owner. Perform all configuration and maintenance activities on the database, and can also drop the database in SQL Server
- db_securityadmin. Modify role membership for custom roles only and manage permissions
- db_backupoperator. Back up the database
- db_datawriter. Add, delete, or change data in all user tables
- db_datareader. Read all data from all user tables
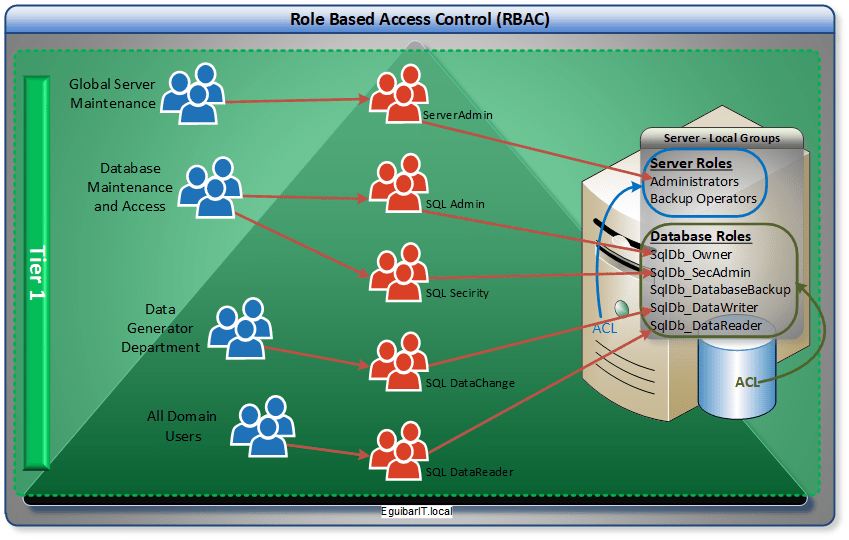
From the 6 role above mentioned, 5 are specific SQL resources. 1 is server default administrator. In this example, we can create the 5 SQL resources as server local groups, and then populate those with Active Directory groups. Now we can have our “Data-Generation-Department” group nested in each of the db_datawriters groups of SQL servers. This group will have evenly granted rights across all SQL servers.