Ok, once we have a little taste of the “sweet Delegation Model” and its tween brother “Tier Model“, you will be having many questions. And questioning is what we need in order to start building a proper Delegation Model with Tiers for Active Directory ®.
As per Peter’s law definition, we will reach the incompetence level in our design. This is because we might not be asking enough questions. By listening to the questions (and why not, even complains) of other teams and stakeholders, we identify areas where not too much is defined.
The Tier Model & Delegation Model questions will help to identify and try to solve these issues.
F.A.Q.
AD Tier Model
Questions raised based on the AD Tier Model. Tier Model is the physical separation of assets. We consider this segregation as the natural extension of the Delegation Model.
Why we need the Tier Model and the Delegation Model.
Any security improvement is welcome, but no single security measurement will help us to protect all our environment. For example, a firewall facing internet indeed will help protecting our network, but will not help us too much on Trojans or worms. This is an antivirus work.
The Tier Model does help us on implementing a set of tiers or buffer zones. And with a set of rules and guides, we can restrict and isolate some of our assets. But here we are missing reducing the overall permissions and rights a user might have. Even if this user is within a given restricted tier. Here is where the twin brother comes to play: the Delegation Model can help reduce the those mentioned permissions and rights.
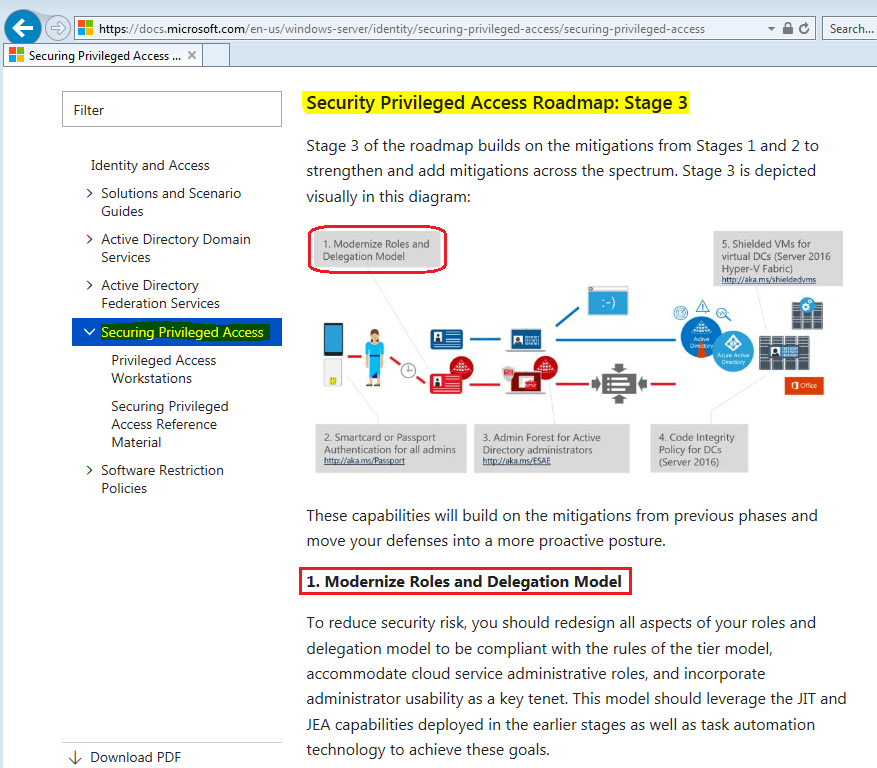
Even more, by implementing both models is not sufficient. We have to be prepared to monitor security, and to properly react on any given event. This demonstrates the need to have several tools (monitoring, analysis, alerting, etc.) working embedded into the models.
Delegation Model
Questions raised on the AD Delegation model. The Delegation Model is to grant controlled and specific rights to administrators, without using privileged groups as Domain Admins. This section will make reference to all topics of the model.
No. Once a user becomes member of a high privileged group, there is no technical restriction. Because of this, she or him can create/change/delete any other administrator. This is the problem with big AD implementations, which did not consider a proper Delegation model (or a 3rd party tool which might provide this functionality).
Restricting Privileged Users is not possible. This is by Active Directory design.
Can we delegate “exclusive” administrator tasks?
Yes. Active Directory is extremely granular when referred to delegations.
We can delegate the task to manage:
- full partition
- certain kind of objects within a given partition
- attribute sets for an object
- specific attributes
Can we have Split-Delegation?
Yes. A split-delegation is when 2 different teams have similar rights within the same object. This is very common and recommended to split loads within teams.
A very common scenario is:
- the user provisioning team is in charge to create and delete users
- Service Desk team in charge to reset passwords and unblock user accounts
- Human Resources team who will maintain certain attributes for the user. This could be be the Employee number and type or the organizational description.
In this example, we can see the importance of the “To who do I need to delegate?” and “What it has to be delegated?” questions
- one group is in charge of granting and revoking access
- a different team manages the user provisioning
- several teams take care of desktops and laptops
- several teams are responsible for the servers
- individual teams are responsible for the infrastructure
Security Concern
Security topics, questions, answers, discussions and references around the model, and the security improvements that can be achieved.
Not really. The model focuses on many “very old, but STILL valid” concepts, which help us to protect our directory. For example, having unpatched systems will render into vulnerable systems, and the only solution is to patch them, reducing the risk thus increasing security.
But when a more advanced thread is ahead, the solutions get more complex. The main concept here is: if you cannot access it, then you cannot tramper with it. The model is restricting highly targeted identities (nice cookie for hackers), minimizing their exposure. The model can be somehow modified and adapted, but there is no other “efficient” alternative to the concept.
Why do I need this model?
Because Active Directory is exposed, and don’t misunderstand this. It is exposed to persons, applications, services and networks, so there is a real risk to get it compromised. There are hundreds of details to take into account to objectively check the risk, but the risk is there, and the best thing to do is to manage the risk.
In the old times, just by having an antivirus was enough (Huuh!) to be protected. No internet available. Networks where pretty small, or even inexistent. As the devices where expensive, granting access to anyone was not so easy, so physical security was kind of present.
Today, we have an extreme connectivity, with at least 1 antivirus, anti-Trojans, worms, rootkits, spam… we have access control list for disks, groups, shares, mailboxes… we have many web applications and services, which use any kind of authentication and authorization… databases… social networks… BYOD… AND we have to manage it, assuring the integrity and security of all these. We cannot afford the risk of exposing all this information, or even worst compromising it.
We care about firewalls… networks… IDS… personal FW… antivirus… Authentication… Authorization… so: Why we are not protecting one of the most valuable and critical assets?
This model will not be the “ultimate” security for AD, but will help mitigate credential theft techniques.
Delegation Model vs. Tier Model comparison
| Delegation
Model |
Tier
Model |
|||
| Lest Privileged Access | ||||
| Logon Restrictions | ||||
| Clean Source Principle | ||||
| Operational Practices | ||||
| Configuration over Convention | ||||
| Segregation of Duties | ||||
| Segregation of Assets | ||||
| Reduce Privileged Accounts | ||||
| Protect from Credential Theft | ||||
| Logical Perimetral Network | ||||
| Auditable Access |