Old physical concept transformed into new Logical technology
When I was first hired on a Fortune500 company, my colleagues from the networking team were heavily involved into something they called “Perimetral Security”. It took me just a snap to realize the concept (Logical Perimetral Security), which by the way, it was very clever.
The main idea of this concept was to organize the network in such way that the “entry/exit points” (as the internet connection, just to name one) which is unsecure, be on the outer most part. Then, between each outer and inner ring, set several tools and mechanisms to keep traffic standard according to previously established rules. Each little piece of the network was re-designed to fit into this ring of rings design, having some assets on the exterior ring, and some other on the inner ones, but the closer to the center the ring is, the more secure and protected these assets on these rings became.
Neuron fight result… an idea
Well, our Active Directory is considered an application, and it only belongs to a given ring within this model… or at least this was my original thought. “It would be very nice if we could separate the directory into several security rings… but AD are full boxes… cannot split a server… really?”
Although AD are full servers, which by definition cannot split, we could go logical, and create such ringing separation inside AD itself. I realized there is no straightforward way to segregate AD, but by following best practices as Segregation of Duties, Roles, Least Privileged Access, 0 Admin model, and having enough convention & configuration, we could architect a useful design.
What would I do if I’m working for you
It took me some time to figure it out, and read many documentations that might give me some clue. Then I came across a Microsoft document which explained how to separate AD stuff into different sections. This is one version of the “Logical Perimetral Security”, but having different views of a single idea is what will help differentiate one model from another.
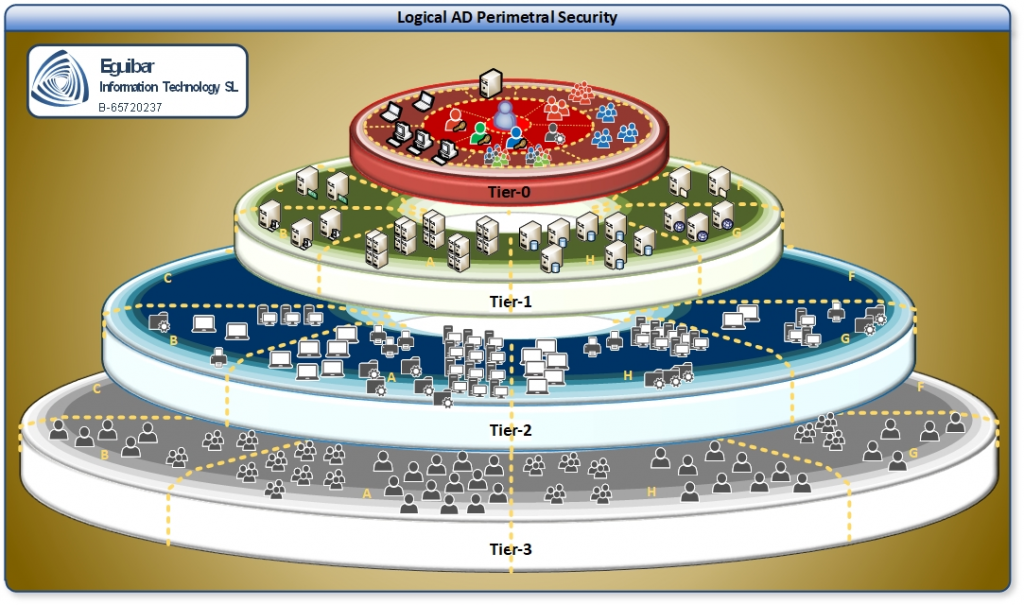
The idea is quite simple (while the implementation might not):
- Identify all your AD assets. Call it asset to any AD user, Group, Computer, Printer, share… or any physical device joined to the domain… or that might be using AD on any form.
- Separate and organize objects into several categories, areas or tiers, going from the least critical up to the most ones.
- Non privileged users
- Non privileged workstations & laptops
- Servers, going from small scopes to widely used ones, even if those are not windows, but using AD somehow
- Services (most likely based on the earlier mentioned point) and how “critical” those are
- Privileged accounts. Not only the mighty Administrator, but all other powerful roles as Server Operators, Account Operators or Backup Operators, just to name some
- Restrict the access and usage of the inner rings on the model.
- Avoid having single teams crossing areas, or even sections within each area.
- Check, Audit and Repeat, always repeat. Make sure your designed model remains over time.
- Restrict the access and usage of the inner rings on the model.
- Avoid having single teams crossing areas, or even sections within each area.
- Check, Audit and Repeat, always repeat. Make sure your designed model remains over time.
What we can Achieve
As we are creating a logical perimetral model within the AD, we must organize the less “critical” assets on the outer-most layer, having a set of buffer zones (Areas and/or Tiers) protecting the inner one. As this is a logical concept, the directory objects are not really “positioned” on these perimeters, but because the computers do access these objects, and distributed across our physical sites, then that exposition (even if real) gets minimized due the fact that the logical objects related are already organized.